Recently, the world’s largest manufacturer of semiconductor chips, Taiwan Semiconductor Manufacturing Co. Ltd. (TSMC), was hit with the WannaCry worm. A supplier installed software containing the infection to a tool and connected it to the network. More than 10,000 unpatched Windows 7 machines became infected, leading to substantial losses in production while machines were down as a result of the worm and the subsequent efforts to repair the damage.
Installing the patches themselves requires taking the machines down and coordinating tool recovery with equipment suppliers.
You can read more about the event here.
As more and more systems in manufacturing facilities are networked together, the threat of worms like WannaCry increases. Managers need to trade off the improved productivity of networked systems against the downtime needed to properly secure those systems against viruses and worms, also considering the threat of greater downtimes from an infection.
Most of the NanoScope® brand AFM’s are controlled by Windows XP computers. Accordingly, the computers supplied by Advanced Surface Microscopy for refurbished systems run Windows XP to retain compatibility with older hardware. Systems installed after May 2017 have the XP WannaCry patch that was provided by Microsoft.
If you have an XP system, here's how to confirm the patch is installed:
If the patch has not yet been installed, then:
Download and install the patch Security Update for Windows XP SP3 (KB4012598).
You can find this at https://www.microsoft.com/en-us/download/details.aspx?id=55245
The file to download is
WindowsXP-KB4012598-x86-Custom-ENU.exe
Date Published: 5/15/2017
File Size: 666 KB
For all other operating systems, go to the authoritative Microsoft page.
Installing the patches themselves requires taking the machines down and coordinating tool recovery with equipment suppliers.
You can read more about the event here.
As more and more systems in manufacturing facilities are networked together, the threat of worms like WannaCry increases. Managers need to trade off the improved productivity of networked systems against the downtime needed to properly secure those systems against viruses and worms, also considering the threat of greater downtimes from an infection.
Most of the NanoScope® brand AFM’s are controlled by Windows XP computers. Accordingly, the computers supplied by Advanced Surface Microscopy for refurbished systems run Windows XP to retain compatibility with older hardware. Systems installed after May 2017 have the XP WannaCry patch that was provided by Microsoft.
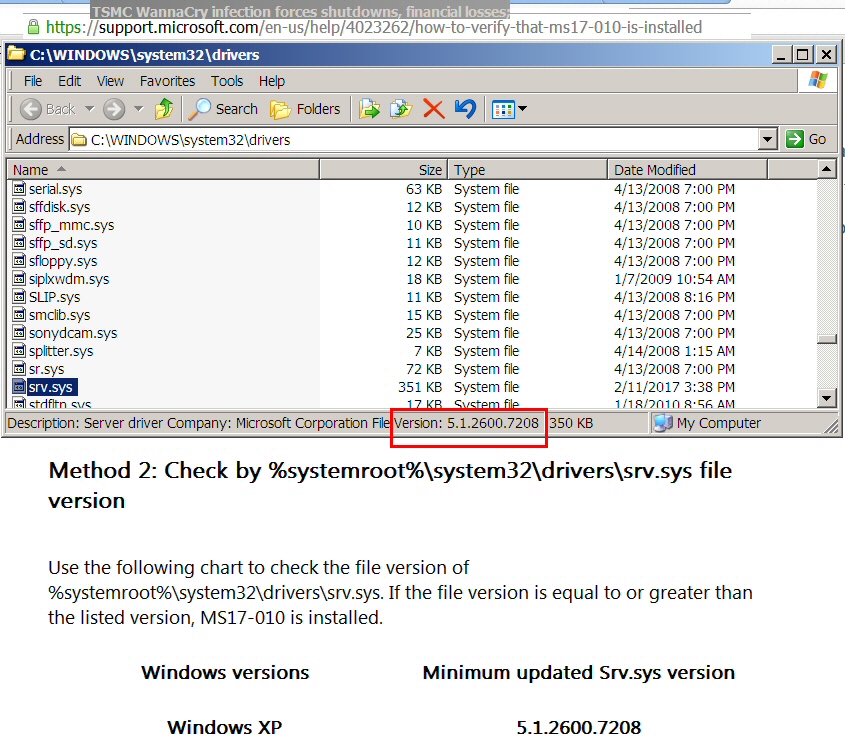
If you have an XP system, here's how to confirm the patch is installed:
- Open Windows Explorer and browse to the indicated folder and file.
- Highlight the file srv.sys and read the file version in the status line.

- Srv.sys version 5.1.2600.7208 is good. If you have this version, the patch is installed.
- Then close the Window.
If the patch has not yet been installed, then:
Download and install the patch Security Update for Windows XP SP3 (KB4012598).
You can find this at https://www.microsoft.com/en-us/download/details.aspx?id=55245
The file to download is
WindowsXP-KB4012598-x86-Custom-ENU.exe
Date Published: 5/15/2017
File Size: 666 KB
For all other operating systems, go to the authoritative Microsoft page.


